From the Zero Trust approach to the Trustless Computing Paradigms
ABSTRACT: In this post, we explain how we share the same “never trust, always verify” philosophical apporach to IT security with the Zero Trust security model, and how Trustless Computing fully recomprises Zero Trust, extends it, makes it certifiable, to move IT security to a next level. We expand such trustless approach to the “check points” components of the Zero Trust architecture. It applies that same trustless approach, via uncompromising “security-by-design”, to all critical technnologies and processes critically involved in the life cycle and supply chain of a target IT system, service or experience. As opposed to Zero Trust, it represents not only an approach but also a certifiable trustworthiness that an IT service can be assess to satisfy at a given time, as per detailed requirements set by a trustworthy Trustless Computing Certification Body, according to its Trustless Computing Paradigms.
Zero Trust is a novel approach for the design and implementation of IT systems and networks that has become dominant in the US, and consequently in Europe as well.
Zero Trust assumes that any network protections can be breached and endpoints in the network can be compromised. For every access-controlled request by an endpoint to another, in a network, it is assumed it could be maliciously spoofed by an attacker. Every request is handled with the principle “never trust, always verify”.
More recently, several large IT security vendors have rightly extended such a paradigm to the endpoint itself, treating the critical internal communications between endpoint components with the same principles.
These assumptions are just about warranted, given what we have learned since Snowden.
Zero Trust therefore suggests that IT systems implement fine-grained access controls and identity governance, micro-segmentation, software-defined perimeters, and anomaly detections via a pervasive network of “checkpoints”, to be placed at as many junctures of a network, and inside endpoint, as much as it is practical.
A city without doors and windows and checkpoints at every street corner?
In a way, Zero Trust is like the government trying to maintain law and order in a city where all windows and doors are compromised or non-existent and all fences have holes, and levels of poverty, inequality and perceived injustice are high.
The only thing it can do is have cops (not private guards!) at all major intersections, to oversee everyone, and stop all or large number passers-by to verify if they have valid IDs, if they are carrying stolen goods or an illegal weapon. Or possibly having one straight in the center of the living room for highly-targeted homes.
In short, Zero Trust is like security in the West Bank in Israel, with checkpoints at every street corner. Perceived injustice and violent political activity forces Israeli police to vet every citizen 24/7 via checkpoints at all major cross-roads, physical and digital, manned by Israeli police or intelligence. This approach to security is likely inevitable in the West Bank today, given its history.
Collateral Damages
For the same reason, it feels that the Zero Trust approach and all those checkpoints are needed given the very sorry state of our IT security whereby all IT and IT standards are painstakingly, regularly weakened or kept weak by powerful nations to fight terrorists and enemy nations.
But having police checkpoints at every street corner, as for every IT network juncture, cannot by itself provide a satisfactory public safety, and it causes very major collateral damages in terms of both civil rights and public safety that may even be superior to the security value-added it brings. The introduction of checkpoints at every street corner, in an IT system as in a city, introduces a huge problem of additional attack surface and accountability of the checkpoint systems, companies and people manning those checkpoints, and the tech they use.
Such problems are multiplied when, as today, such check-points are made by private companies, domestic and foreign, and are not subject to trustworthy socio-technical standards. The Director of DARPA’s High-assurance Program estimated in 2016 that 30% of vulnerabilities in high-assurance systems are due to cybersecurity solutions introduced inside and between them. So therefore in many cases it is hard to know if the insecurity introduced is more or less than the one mitigated.
Diagram by Boris Taratine showing some limitations of the Zero Trust model
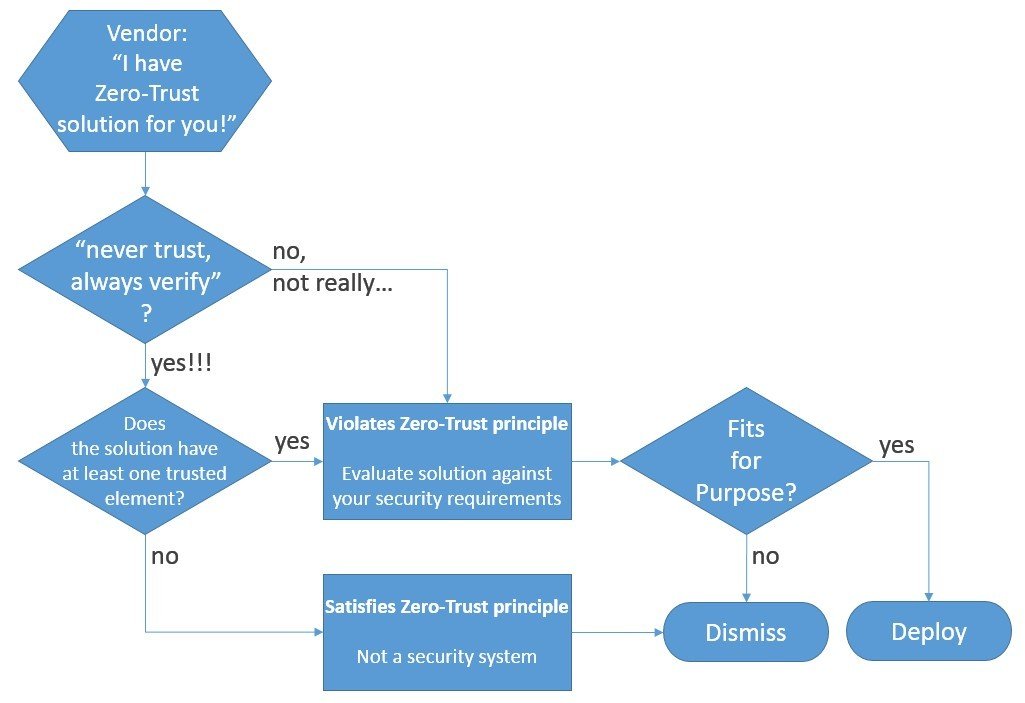
Here is a diagram from a recent post by Boris Taratine, advisor to the Trustless Computing Association, which explains key conceptual contradictions of the Zero Trust model, highlighting how the new components or component features that it recommends to introduce are not also subject to the same “never trust, always verify”.
This Zero Trust's root conceptual flaw is remarkably similar to that of Huawei's ABC Principles for Security, its much-advertised cybersecurity mantra, where ABC stands for "Assume nothing. Believe no one. Check everything". It is an agreeable approach at first sight but then, unsurprisingly, Huawei's technologies, Huawei's lead technical staff and architects, Huawei's management, Huawei's ownership and Huawei's overbearing government are excluded from the assuming, the believing and the checking.
Trustless Computing
What if we further extended “never trust, always verify” to include the IT components introduced to implement the Zero Trust components themselves AND to all the critical components of the target IT systems, and subjected them to extreme security review in relation to complexity?
No need to invent anything new. We had great success already in other sectors like commercial aviation, nuclear and paper-based electoral systems, just applying transparency, battle-tested components, and complexity minimization. Plenty of high-assurance battle-tested open-licensed components are available today.
The obstacle is not technical. As we said before, even the most high-assurance IT and IT standards are weakened by design for very valid reasons by powerful nations.
So therefore the implementation of uncompromisingly trustless technical and procedural paradigms - as it has been done in other critical sectors - will never happen if it does not also provide a reliable solution to enable legitimate lawful access. In fact, the assumption “never trust, always verify” should also apply to the end-user, who could be a terrorist or an enemy, which is utilizing strong encryption to plot a major attack.
After the US government tried and failed to introduce the Clipper Chip as a way to enable legitimate lawful access in digital communication systems - as it had existed in mail and analog telephone for decades - a few dozen IT security experts from the US and civil rights and democracy activists produce foundational papers to detail very many dangers and complexities of any conceivable mechanism, technical and socio-technical, that the government may propose in the future
The US government found that weakening all IT, to the extent they could keep the vulnerabilities for themselves, provided even more freedom to leverage its informational superiority for their legitimate national security objectives, and also illegitimate but yet to be proven unconstitutional in the US as we’ve learned after Snowden.
Experts and privacy activists thought they had won the “Crypto War”, but instead we ended up in a World where even and especially millions of the most sensitive citizens have no other choice but use IT systems that have everywhere bug-doors (i.e. vulnerabilities willingly inserted or let be that are disguised as errors), and the current disaster of IT security and privacy that we live in.
For these reasons since 2015 our Trustless Computing Association has been leading research initiatives, and a global conference series with experts and nation state representatives, to validate the possibility that a solution may be worth trying, for a specific class of IT systems, with a careful and sophisticated approach based on transparency and battle-tested technology, methods and safeguards.
As detailed in the abstract of our 2018 Position Paper for a Trustless Computing Certification Body, we argue that applying to in-person, procedural legitimate lawful access mechanisms for a target IT system, the same extreme socio-technical safeguards that are needed to ensure the utmost privacy and security - exclusively for highly-minimized systems for human communication meant for the highest security and privacy - may “overall reduce the risk of abuse of end-users by anyone to levels that are radically (or at least substantially) lower than any of the other alternative secure IT systems – available today or knowingly in development – which do or do not offer such voluntary processing”.
That’s why we established the in 2015, elaborated the Trustless Computing Paradigms, and the Trustless Computing Certification Body, established last June 2021 in Geneva, and are building initial compliant IT systems via its “spin-in” TRUSTLESS.AI, in the form of a 2mm-thin mobile device and related cloud infrastructure that will be embedded face out in your future smartphone and that of everyone, finally enforceing the principles of freedom and democracy in Cyberspace.